Over the past few weeks I’ve received a large percentage of phishing emails at my emailanswers.com corporate email account that purport to be from American Express, although they are not. These emails are sent by scammers trying to steal user names and passwords from unsuspecting American Express card holders, so they can then access their account information and card numbers to use them for fraudulent purposes. Below is a sample of one of the many phishing emails I received.
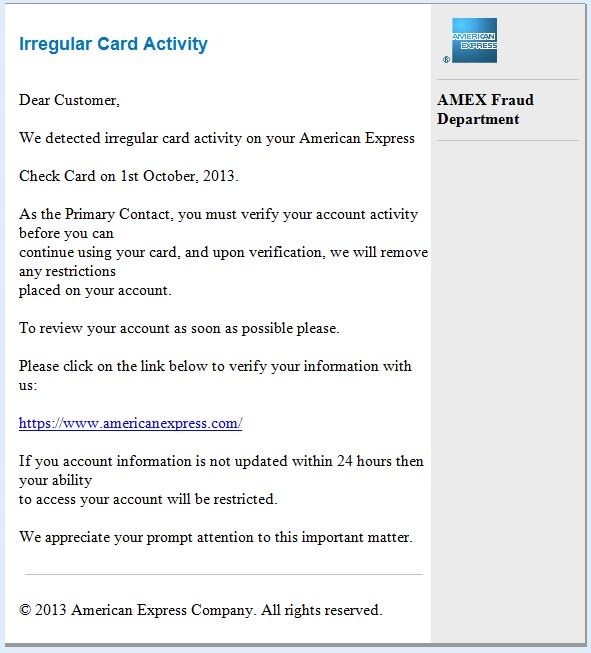
Although it is pretty obvious to me that this email is not from American Express and is no doubt a phishing email, there are some recipients who are not so astute. If your mother, grandfather or someone new to the Internet or not paying close attention received this email, would they be able to tell that it was not sent from American Express? Would they click the link that looks legitimate and appears as if it would take them to the American Express website? Even though it will not take them to the real American Express website, will they unwittingly type in their user name and password on the fake site? Obviously a percentage of people do, because if they didn’t, these phishing emails would cease being sent.
Below is the header that was received with this email:
From: American Express [mailto:[email protected]]
Sent: Tuesday, October 09, 2013 12:15 PM
To: [email protected]
Subject: Fraud Alert: Irregular Card Activity
Based on the received ‘from name’ and ‘email address’, it looks like the email was sent from American Express. It even has an aexp.com email address, which is the domain American Express uses to send emails from. It’s not that I blame American Express for sending this email, but rather American Express could easily stop this email from being delivered if they would simply fix their SPF Records. You might ask yourself at this point, how can you blame American Express if they didn’t send this email? Hang in there for 2 minutes and I’ll tell you. Let’s review a few details first.
OK, so what is an SPF Record?
An SPF (Sender Policy Framework) record is a DNS (Domain Name System) record which lists specific servers and IP addresses that are allowed to send e-mail from a domain, such as aexp.com. Correctly configured, this reduces spam and phishing activity that may be perceived to originate from a specific domain, that actually doesn’t, which is known as source address spoofing.
An SPF record is used for messaging security purposes. The SPF record enables a receiving email server to query DNS and determine whether the sending server is authorized to send from a specific domain. There are three ways in which an SPF record can be parsed and dealt with; such as hard fail, soft fail or neutral. The difference between a hard fail and a soft fail is how the owner of SPF records expects the message recipients to treat a spoofed message. When a neutral response is received, it usually means that no SPF record exists for the domain. Most email servers will accept an email with a neutral SPF response, but most SMBs and large corporations all have published SPF records.
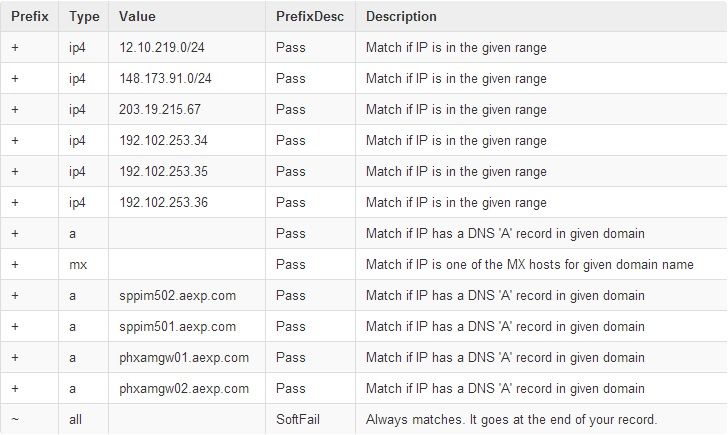
Below is a list of SPF Records for aexp.com, which is used by American Express to send email.
“Spf2.0/pra a:phxamgw01.aexp.com a:phxamgw02.aexp.com a:sppim501.aexp.com a:sppim502.aexp.com ~all”
“v=spf1 ip4:12.10.219.0/24 ip4:148.173.91.0/24 ip4:203.19.215.67 ip4:192.102.253.34 ip4:192.102.253.35 ip4:192.102.253.36 a mx a:sppim502.aexp.com a:sppim501.aexp.com a:phxamgw01.aexp.com a:phxamgw02.aexp.com ~all”
To simplify and make the records easier to decipher, I have broken down the formatted records into an easy to understand format.
Without getting into too technical an explanation of how an SPF record is configured, I’ll discuss and point out the failure. If you look at the last line in the SPF record detail above, you’ll notice ~all which is listed as a “Soft Fail”.
Understanding the difference between ~all Soft Fail and -all Hard Fail
A Soft Fail (~all)
If the email message from a domain comes from an IP address which is outside the IP range that is defined in the SPF record for the domain, the message will be accepted but marked in the email header. This is something you do not see when you receive the email. All properly configured email servers will accept an email tagged with a “Soft Fail”.
A Hard Fail (-all)
If the email message from a domain comes from an IP address which is outside the IP range that is defined in the SPF record for the domain, the message will be rejected.
How American Express has failed to protect its card members.
If American Express simply changed their SPF Record from ~all (Soft Fail) to –all (Hard Fail) these fraudulent, phishing emails, that appear to be sent from American Express, would be rejected at the recipients email server and never get delivered to the intended email recipient. Simply using ~all is tantamount to saying, here are all the possible servers that our email should come from, but if it doesn’t accept it anyway. Why even bother publishing SPF records if you’re going to override them with a ~all?
American Express has a section on their website dedicated to fraud prevention and protecting your information. They provide advice and a vast amount of information to help you protect yourself, but fail miserably themselves where it really matters.
In 2012 alone, losses from credit card fraud totaled $6 billion. Now who do you think pay’s for those losses? You are correct, we all do. If by simply changing a tilde (~) to a dash (–) or ~all to -all (Soft Fail to Hard Fail) American Express could reduce the number of phishing emails delivered and significantly reduce credit card fraud and losses due to stolen credit card information. Why wouldn’t American Express make this simple change? Don’t know? Neither do I.
“It is the obvious which is so difficult to see most of the time. People say ‘It’s as plain as the nose on your face.’ But how much of the nose on your face can you see, unless someone holds a mirror up to you?”
― Isaac Asimov