Studies continue to show that insiders – whether regular employees, IT staff or contractors – can be just as or more damaging to an organization as outsiders. And it isn’t just malicious employees intending to directly harm the company through theft or sabotage. These insider threats can be completely unintentional as well by employees who lack training, are easily socially engineered or who are negligent or forgetful.
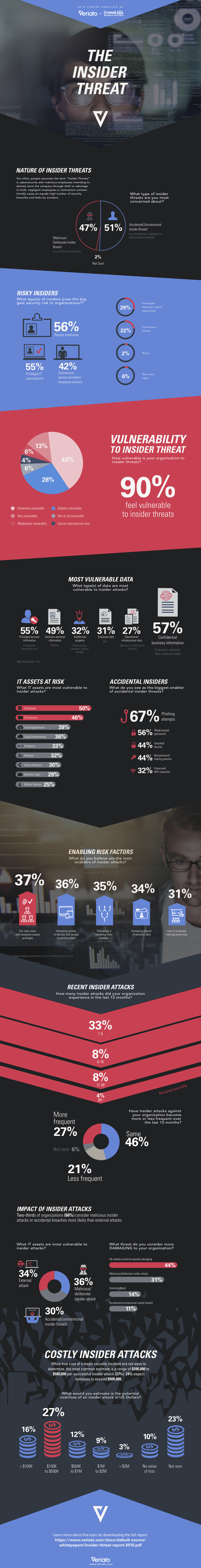
As the 2018 Insider Threat Report infographic below shows, 90 percent of organizations still feel vulnerable to insider threats, with 53 percent saying they’ve had one or more attacks in the last 12 months, and 27 percent saying they’re becoming more frequent. Confidential business information and privileged account information is cited as the most vulnerable to data loss, with the biggest enabler of accidental insider threats being phishing attempts, weak passwords, unlocked devices, bad password sharing practices and unsecured Wi-Fi networks.
Fortunately, companies are starting to recognize the problem and are putting into place various detection measures to prevent breaches, however not enough companies are putting in the right measures.
So what are they doing?
According to the report, companies are implementing software such as data loss prevention(60 percent), encryption (60 percent), identity and access management (56 percent), and endpoint and mobile security (50 percent). They are also using detection controls such as intrusion detection and prevention (63 percent), log management (62 percent), security information and event management (51 percent), predictive analytics (40 percent), and user and entity behavior analytics (UEBA) (39 percent).
While data loss prevention (DLP) plays a role to protect from insider threats, robust insider threat programs need to focus on data, device AND the user, not just data. UEBA focuses on the user, providing anearly warning of suspicious conduct by analyzing human behavior—both technical and psycholinguistic indicators—for warning signs of changes that are directly related to insider threats. It analyzes insider behavior, detects anomalies, and provides actionable alerts when behavioral shifts suggest insider threats. It can work with employee monitoring software to provide unmatched visibility into the online and communications activity of these employees and contractors.
The number of companies actually using UEBA has more than doubled in the last year or so, according to stats the Insider Threat Report, but that number is still lower than nearly every other detection solution.
What is your company using to prevent losing your confidential information to insider threats?
