Verizon’s 2019 Data Breach Investigations Report states that 80% of hacking-related breaches come from weak or stolen credentials. How can you protect your application when the entry point is so vulnerable? Multi-factor Authentication (MFA) is the solution. With its strong security layers, it provides safe authentication for digital services. It is slowly becoming the standard for security. Have you ever received a One-Time Password (OTP) via SMS when logging into an app? That’s MFA in action!
Last year, Microsoft announced that MFA is required for Privileged Accounts, and six months later, they extended this requirement to Cloud Solution Provider (CSP) program partners. Let’s look at why MFA is a smart security choice, especially if you work with a Microsoft CSP partner or Managed Service Provider (MSP).
Passwords will be compromised, MFA goes beyond
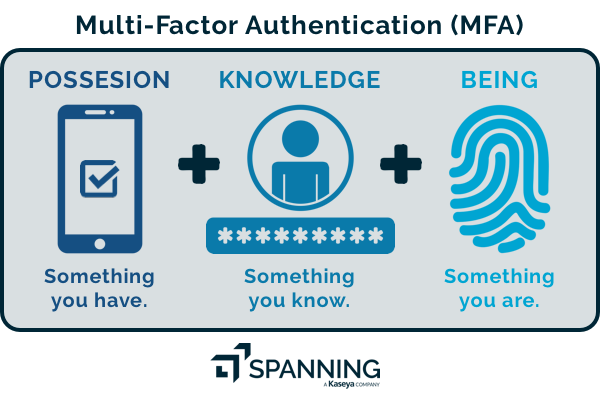
MFA does not rest the security of your entire application on one password, which inevitably is weak, no matter how “strong” it is. MFA combines what the user knows (password), with what the user has (security token) and what the user is (biometric verification). Access is granted only after an additional factor is verified such as a one-time password (OTP) sent via SMS, and can also include a biometric check like a scan of the fingerprint or retina. Studies indicate that MFA blocks 99.9% of malicious attacks – and this applies not just to Microsoft accounts but to any user profile on a digital application. As Alex Weinert, Microsoft’s Group Program Manager for Identity Security and Protection says, “Your password (rules) don’t matter, but MFA does. Go turn on MFA if you haven’t.”
MFA Secures and Streamlines the User Experience
MFA not only secures your app but provides a seamless User Experience (UX). It skips the onus of having complex passwords, which is a huge improvement in UX. While the user feels safer in the knowledge that they’re accessing a secure app that will protect them from identity theft. There are a number of options for the extra layer(s) of authentication that does not compromise on experience – via an OTP, scanning a fingerprint/eye, answering a security question, using a VPN device or a USB hardware token.
Are your third-party CSP apps putting your company at risk?
MFA holds particular importance when applied to Microsoft’s CSP. When a company purchases Office 365 licenses from a reseller or partners with an MSP, the partner is granted administrative privileges. This means that your service partners have full access to your organization’s email, files, accounts and sites stored in the cloud. If one of your partners or partner’s solutions are compromised, it would, in turn, mean that you are compromised. Recently, a breach at PCM, the world’s sixth-largest CSP, caused a breach at one of their client’s firm when “the attackers stole administrative credentials that PCM uses to manage client accounts within Office 365”. Such attacks have further highlighted the vulnerabilities in the CSP world.
Hence, it is in keeping with Microsoft’s commitment to keeping its products safe for customers and partners that it should extend its security best practices to the partner ecosystem too. Microsoft has mandated that “All users in partner tenants must use Multi-Factor Authentication (MFA) when signing into Microsoft commercial cloud services or to transact in CSP through Partner Center or via APIs. Through the enablement of the baseline protection policies MFA is available at no cost for all users of partner tenants.”
Check on your third-party applications, and ensure that they support MFA. Assess that all your CSP partners leverage policies such as the ‘Require MFA for admins’ baseline policy to administrative users in the partner directory. Partners can choose any MFA solution that is compatible with Azure Active Directory (AAD). Read here for an exhaustive list of partner security requirements.
Moreover, if your vendor is not using OAuth, but Service account, it can cause a disruption of service as MFA being enabled on a Service Account may cause the application to break.