Researchers at Israeli firm EVA Information Security found that nearly 3 million iOS and macOS apps were exposed to supply chain attacks. Here is everything we know about the issue and whether Apple device owners should be worried after the findings.
The threat involves CocoaPods – an open-source dependency manager – that programmers use to incorporate existing software libraries into apps. Over three million apps were coded in Swift and Objective-C using CocoaPods which is the most popular platform among iOS developers.
According to EVA, it contains three vulnerabilities, one of which was around for a decade. These flaws allowed “any malicious actor to claim ownership over thousands of unclaimed pods and insert malicious code into many of the most popular iOS and MacOS applications.”
Researchers painted a grim picture of how severe the attack was and, in its blog post, EVA said, “Such an attack on the mobile app ecosystem could infect almost every Apple device, leaving thousands of organizations vulnerable to catastrophic financial and reputational damage.”
It further added that one of these vulnerabilities could have allowed zero-day attacks against the “most advanced and secure organizations’ infrastructure.” The existence of this magnitude of a vulnerability is a bit terrifying, but you don’t have to start panicking just yet.
https://Twitter.com/TheHackersNews/status/1807810357307531432
Attackers Could Target Most Apple Devices Using One Vulnerability
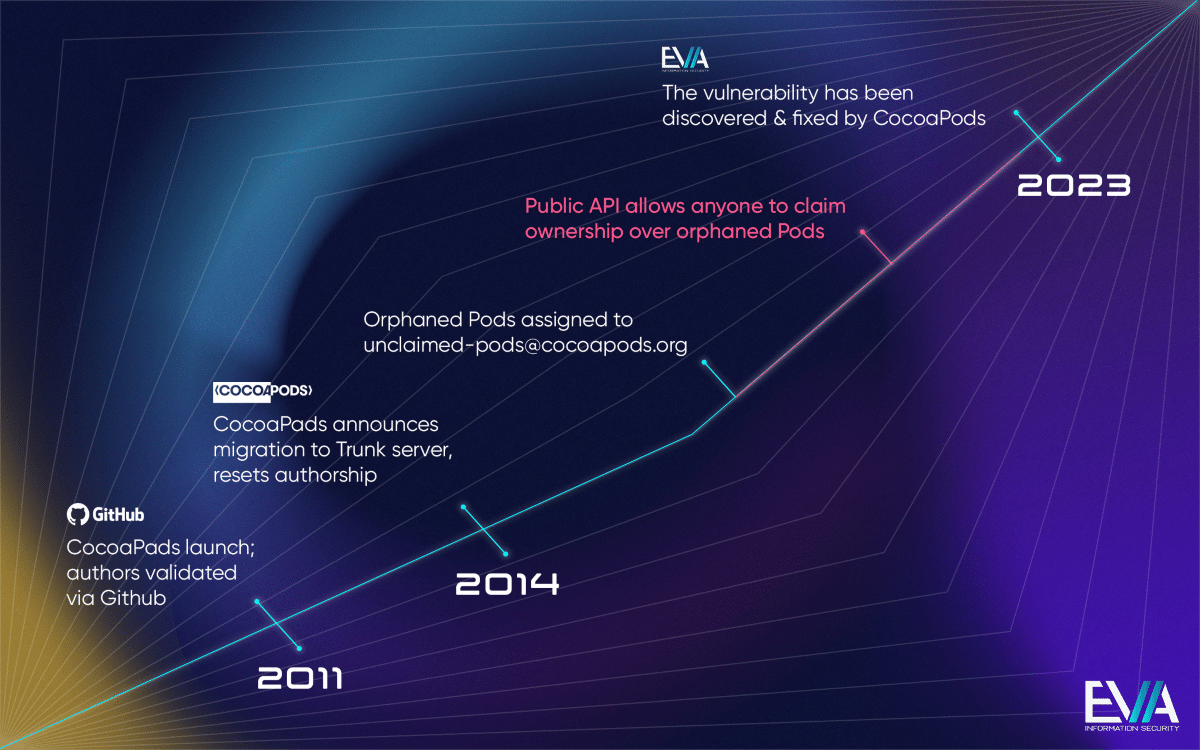
The first vulnerability has a CVSS (Common Vulnerability Scoring System) score of 9.3 (10 being the most severe) and is now called CVE-2024-38368. According to EVA, in May 2014, CocoaPods announced a migration to a new ‘Trunk’ server’ and as part of the migration it reset the authorship of all previously uploaded Pods.
Authors were supposed to claim ownership of their pods, but many Podspec authors didn’t. All orphan pods were then affiliated with a default CocoaPods owner with the email id [email protected].
According to EVA, it noticed that the public API endpoint to claim a pod was still available and anyone could claim these orphaned pods without going through due verification. This means that attackers could have wrongfully claimed these orphaned Pods as theirs.
They could then manipulate the source code or insert malicious content in these Pods, which, according to EVA, could “potentially find its way into a large percentage of Apple devices currently in use.”
Second Vulnerability Allowed Remote Code Execution
The second vulnerability which is known as CVE-2024-38366 has a CVSS score of 10 which highlights its severity. It allowed for remote code execution on the Trunk server after a change in the verification process in February 2014. The new process utilized a third-party ruby gem package rfc-822 which has several vulnerable methods.
According to EVA, “If an unauthorized threat actor compromises the server, they could potentially dump all pod owners’ session tokens, poison client’s traffic or even shut down the server completely.”
The third vulnerability has the lowest CVSS score of 8.2 and is associated with the Trunk server’s own source code. The vulnerability which is named CVE-2024-38367 allowed attackers to take over the owner accounts to trigger supply chain attacks that could have an impact across Apple’s ecosystem.
By exploiting this vulnerability, attackers could fully take over all the CocoaPods owned by the account, which they could manipulate to create a massive disruption within the CocoaPods ecosystem.
Should Apple Device Owners Be Worried?
While these vulnerabilities look spooky, Apple device owners should get overly worried as according to EVA, there is “no direct evidence of any of these vulnerabilities being exploited in the wild.” It, however, stressed that “evidence of absence is not absence of evidence.”
Meanwhile, the vulnerabilities were fixed in October so no action is required on the part of Apple device owners who were using one of these apps. The report however yet again shows the vulnerabilities of open-source projects that are invariably maintained by volunteer programmers.
However, the jury is divided on whether open-source projects are less secure than proprietary and closed-door projects. According to We Live Security, the security of software is independent of whether it is open or closed source.
It however added, “What matters is the process through which software is developed, and fixes are implemented for vulnerabilities. The reliability of those fixes, and the speed at which they can be implemented, are what organizations should be focusing on in terms of determining a security posture – not the type of software license.”
As for users, while they might not be required to take any actions for these vulnerabilities, they should always follow the basic security drill. This would include keeping the phone software updated, securing the device with strong credentials, and also not downloading any unauthorized apps – especially those that are outside the App Store.