2020 was a banner year for ransomware: good for hackers, bad for the companies trying to ward them off. Ransomware attacks became a matter of not “if” but “when,” with experts predicting a ransomware attack every 11 seconds in 2021. Sophisticated cybercriminals continue to prey on vulnerabilities, and victims are giving in to demands and handing over cash to retrieve their encrypted data.
But paying a ransom doesn’t always guarantee you’ll get all of your data back. The ultimate outcome following a ransomware attack really hinges on how well you’re prepared.
Below, we’ll take a look at how a ransomware attack could affect two hypothetical companies with very different data protection strategies.
Meet Company A and Company B
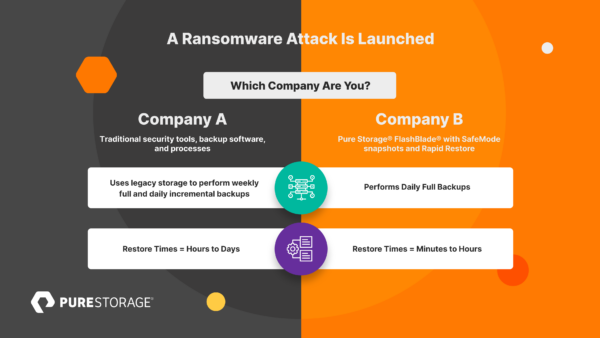
Company A has the latest security tools to safeguard its data, including backup software and processes in place to protect itself against threats and cyberattacks. But is it fully protected from an unsuspecting ransomware attack? And, more importantly, how quickly can it recover?
Company B has deployed similar tools, along with an extra layer of defense—Pure Storage® FlashBlade® with SafeMode™ snapshots and Rapid Restore. The company can use immutable, read-only snapshots from its frequent system backups to quickly recover its data.
Hour Zero
It’s a very real-world scenario: A cybercriminal gang launches a weekend attack when IT staff isn’t on duty. Once they’ve breached the company’s network, the hackers laterally hit as many workstations as possible, installing ransomware on all systems.
By the time security alerts sound, the ransomware encryption process is over. The hackers have locked down the network and encrypted system files. No one can access them without the decryption key.
Responding to the Attack
The worst has happened. The companies discover the attack and receive instructions for the ransom payment. Hackers threaten to destroy the companies’ data if they don’t receive payment by a specific time.
Both companies have security teams, monitoring systems, and backups, but their data security architectures and capabilities are quite different. Here’s how things play out for our hypothetical companies from this point:
Company A looks to leverage backups that reside on secondary storage, but they aren’t readily accessible. This slows time to recovery. Additionally, they must run forensic analysis to find the attack origins to ensure they don’t restore a corrupted backup.
Company B’s frequent backups have safeguarded critical data. Because SafeMode snapshots can’t be modified, deleted, or encrypted, the company has a secure copy of data that’s readily accessible. They’re able to leverage snapshots to conduct high-speed forensic analysis that allows them to quickly restore a clean backup.
Weighing Options
It’s time to assess the damage, triage issues, and determine how to proceed. Unfortunately, negotiating with cybercriminals is rarely an effective strategy. In some cases, companies that pay ransoms never fully recover their data. And according to the Sophos State of Ransomware 2020, paying the ransom can even double the total cost of recovery.
Company A’s IT security team discusses options. Either it can pay the ransom and hope the cybercriminals will decrypt the files, or it can attempt recovery by removing infected files and restoring data from backups. The problems stack up:
- Risk of reintroducing malware from backups. Backups have to be cleaned before recovery, or you risk reintroducing malware back into the system as part of the recovery.
- Costly downtime: Right away, it’s looking like recovery point objectives (RPOs) and recovery time objectives (RTOs) won’t be met. IT resources are diverted as purpose-built data-protection infrastructure gets over-stressed by the weight of the attack.
- Missed SLAs: With networks and critical apps out of commission, SLAs are missed. This isn’t just an IT problem, it’s a business problem—resulting in lost customer confidence and lost revenue.
Company B continues to implement its plan of action using SafeMode snapshots to conduct forensic analysis and quickly restore clean backups. This built-in feature provides read-only snapshots of backup data and associated metadata catalogs locally without having to go to other platforms. As a result, the company can meet even the strictest RPOs and RTOs, and operations aren’t disrupted by a prolonged outage.
Swinging Into Action
The focus is now on restoring data. Yet, the recovery process can become much more complex when backups are also encrypted.
Company A decides to recover infected files and restore data from its backups. But the company quickly discovers that the backups are also encrypted because they were connected to the network. This includes end-user primary data, as well as NAS file systems and object stores.
Company B also discovers that its backups are encrypted, but thanks to SafeMode snapshots, they’re protected. Ransomware can’t eradicate, modify, or encrypt them, even with admin credentials. Database backups are restored.
The Path to Recovery
When it comes to maintaining business continuity, every minute counts. For many companies, the average downtime following an attack can last five or more days—sometimes even longer.
Company A is now facing significant downtime with a long process of cleaning up and recommissioning systems—and restoring data. Infected backups complicate the situation. Not all data is restorable.
The company pays the ransom, but decrypting the files is an expensive, time-consuming task. Unfortunately, the ransom payment becomes public knowledge, negatively impacting both the company’s reputation and bottom line.
Company B can seamlessly roll into recovery mode. With FlashBlade, it benefits from 270TB/hour data-recovery performance, enabling a rapid recovery of data. Within hours, Company B’s Tier-1 dev/test environments, analytics, IT sandboxes, and backups are recovered. Critical apps are back up and running, and teams get back to work. Without internal loss of confidence in the IT team or public loss of confidence in the wider business.
Which Company Would You Rather Be?
A ransomware attack is a risk you can’t afford not to be prepared for. Chances are, no one wants to be like Company A. But there are a lot of Company A’s out there, and they may not even know it. You may think you’re doing all the right things to stay secure, but relying on legacy security architectures won’t protect you from modern attacks. Only modern solutions like SafeMode and Rapid Restore can take your security strategy to the next level.
Make 2021 the year you beat downtime—and potential hackers—and be like Company B with ransomware recovery from Pure Storage. You’ll get an unmatched level of preparedness and ensure your data is always ready and available in the event of a ransomware attack.
- https://cybersecurityventures.com/cybercrime-damages-6-trillion-by-2021/
- https://www.sophos.com/en-us/medialibrary/Gated-Assets/white-papers/sophos-the-state-of-ransomware-2020-wp.pdf
- https://www.veritas.com/content/dam/Veritas/docs/ebook/V1117_GA_EB_2020-ransomware-resiliency-report_EN.pdf