A devastating widespread attack is rippling throughout the decentralized finance (DeFi) space. The attackers were able to replace well-trusted platforms with wallet-draining websites using a sophisticated domain name system (DNS) hijacking attack, potentially affecting over 200 different DeFi protocols.
News about the situation started to surface on July 11 when several users of DeFi applications began reporting that they were being redirected to fake websites.
https://twitter.com/MetaMask/status/1811436757759701391
The event has uncovered critical weaknesses in the IT infrastructure supporting the most popular protocols in this space like Compound Finance, the Celer Network, and even the popular crypto wallet MetaMask.
Compound Finance Among the First to Report the Attack
The attack first came to the attention of security researchers when users attempting to access Compound Finance, one of the largest lending protocols in the DeFi space, were redirected to a malicious website. This fraudulent site contained a “drainer” application designed to steal users’ assets once they provided their access credentials to access or link their wallets.
As news of the Compound Finance breach started to spread, it quickly became apparent that this was not an isolated incident. The Celer Network, a blockchain interoperability protocol, announced that it had been targeted by the hackers as well. However, its domain monitoring system successfully intercepted the takeover attempt before any damage could be done.
Meanwhile, later that day, the blockchain security platform Blockaid issued an alert indicating that several front-end interfaces of DeFi protocols were either at risk of being hijacked or had already suffered a breach.
The company’s initial assessment suggested that the attackers were exploiting vulnerabilities in the DNS records of projects hosted on Squarespace, a popular website-building and hosting service.
Over 200 Protocols Could be at Risk of Suffering a DNS Attack
As the crypto community struggled to determine how far the attack had gone, a developer from the blockchain analytics firm DefiLlama with the pseudonym “0xngmi” provided a list of protocols that could have been affected by the attack.
compiled a (partial) list of domains connected to square space that would be at risk of being hacked rn, i'd avoid them for nowhttps://t.co/Cih5YTgFL9
— 0xngmi (@0xngmi) July 11, 2024
The list included prominent names in the DeFi space such as Pendle Finance, Polymarket, and dYdX. In total, he claimed that more than 100 different protocols may either be vulnerable or have already been affected by the incident.
Pendle confirmed the attack later by stating that its bot detected that “a new malicious DNS” was added to its DNS record to redirect users to a fake website.
Meanwhile, the co-founder and Chief Executive Officer of Blockaid, Ido Ben-Natan, told Decrypt that the number of affected projects could be twice as high as 228 other DeFi applications were reportedly at risk based on his firm’s findings.
The Attack Vector: Squarespace’s Acquisition of Google Domains
The root cause of the vulnerability appears to be linked to Squarespace’s recent acquisition of Google’s domain registrar business. In June 2023, Squarespace purchased Google Domains for $180 million, a move that brought numerous websites under its management. The migration of these web domains from Google to Squarespace began on July 10, just one day before the attacks were detected.
Security experts have identified a critical oversight in this migration process: the two-factor authentication (2FA) securing websites previously managed by Google was deactivated during the transition. This left many domains vulnerable to unauthorized access and manipulation.
Bobby Ong, co-founder of CoinGecko, summarized the situation on Twitter: “A DNS attack is going on right now affecting Squarespace domain registrar. The best thing to do is to not interact with crypto and rest for the next couple of days until everything is resolved.”
How Does a DNS Attack Work?
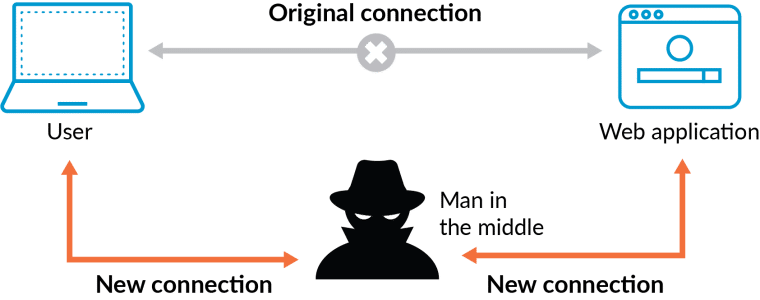
The attackers exploited the temporary lack of 2FA protection to gain unauthorized access to domain settings. Once in control, they were able to modify the DNS records, redirecting users from the legitimate websites of these DeFi protocols websites to malicious clones designed to steal funds.
Blockaid’s analysis revealed that the attackers were using a drainer kit associated with the Inferno Drainer group, a notorious collective known for creating sophisticated phishing and wallet-draining schemes.
The Inferno Drainer kit is designed to trick unsuspecting users into approving transactions that transfer their funds directly to the attacker’s wallet.
The association with Inferno Drainer was confirmed through both on-chain and off-chain evidence, including shared wallet addresses, smart contract similarities, and the use of common IP addresses and domains linked to previous Inferno attacks.
Protocols Tell Users to Avoid Web3 Applications for Now
Most of the affected protocols and the broader DeFi community quickly took action to mitigate the damage of the breach. Compound Finance and Celer Network quickly acknowledged the DNS attacks on their platforms and began investigating the full extent of the breach.
https://twitter.com/compoundfinance/status/1811328333063520683
Both protocols urged users to avoid interacting with their platforms until the situation is fully resolved.
Moreover, the popular wallet provider MetaMask implemented an immediate safeguard, announcing that it would display warnings to users attempting to transact on any known compromised sites. This proactive measure aimed to reduce the risk posed to users’ assets if they were unaware of what was going on.
Are Web3 Applications Safe?
This DNS hijacking attack has surfaced many critical issues that must soon be addressed concerning the security of the web3 ecosystem, including the following:
- Reliance on Centralized Infrastructure: The incident highlights the paradox of decentralized finance applications relying on centralized web infrastructure for their front end. While the blockchain-based smart contracts themselves are still secure, the centralized front-end interfaces proved to be a significant point of vulnerability.
- The Importance of Domain Security: The attack highlights the critical role that domain security plays in the overall safety of DeFi protocols. It should be considered a reminder that even the most robust smart contract security can be undermined by vulnerabilities in the web2 layer.
- User Education and Vigilance: The success of these incidents depends largely on users’ actions. This incident emphasizes the ongoing need for user education and the importance of approaching with caution when interacting with DeFi applications.
- Regulatory Implications: As the DeFi sector continues to grow and attract more mainstream attention, incidents like this may prompt increased scrutiny from regulators who may be concerned about consumer and investor protection.
How to Avoid DNS Hijacking Incidents
As the DeFi community grapples with the fallout from this attack, attention is turning to long-term solutions that prevent similar incidents in the future. Some of the approaches that could help platforms avoid hijacking incidents include:
- Decentralized Domain Solutions: Matthew Gould, founder of Web3 domain provider Unstoppable Domains, suggested that protocols should create verified on-chain records for domains. This could provide an additional layer of protection for browsers that could reduce the risk of DNS attacks.
- Enhanced Authentication for DNS Updates: Gould proposed a feature where DNS updates would require a signature from the user’s wallet. This would significantly increase the difficulty for hackers as they would need to compromise both the registrar and the user separately.
- Improved Monitoring and Alert Systems: The incident highlights the importance of robust monitoring systems that can quickly detect and respond to unauthorized DNS changes.
- Greater Use of Decentralized Hosting: Some experts are advocating for more widespread adoption of decentralized hosting solutions such as the InterPlanetary File System (IPFS).
- Regular Security Audits: Regular and comprehensive security audits should cover not just smart contract code but also the entire infrastructure that currently supports DeFi applications.
The July 11 DNS hijacking attack involving multiple DeFi protocols should alert the entire community about the ongoing security challenges that web3 applications still face regardless of the progress that the ecosystem has made to this date.
As the DeFi sector continues to evolve and mature, addressing these vulnerabilities will be crucial to keep building users’ trust and achieving mainstream adoption.
